Istio set up
Istio is a service mesh that provides a secure, high-performance networking platform for microservices and applications running on Kubernetes.
Node port solutions can work in the short term, but they are not long-term solutions, neither for production, as they require opening up multiple ports to the public internet.
The following diagram represents the architecture with Istio configured
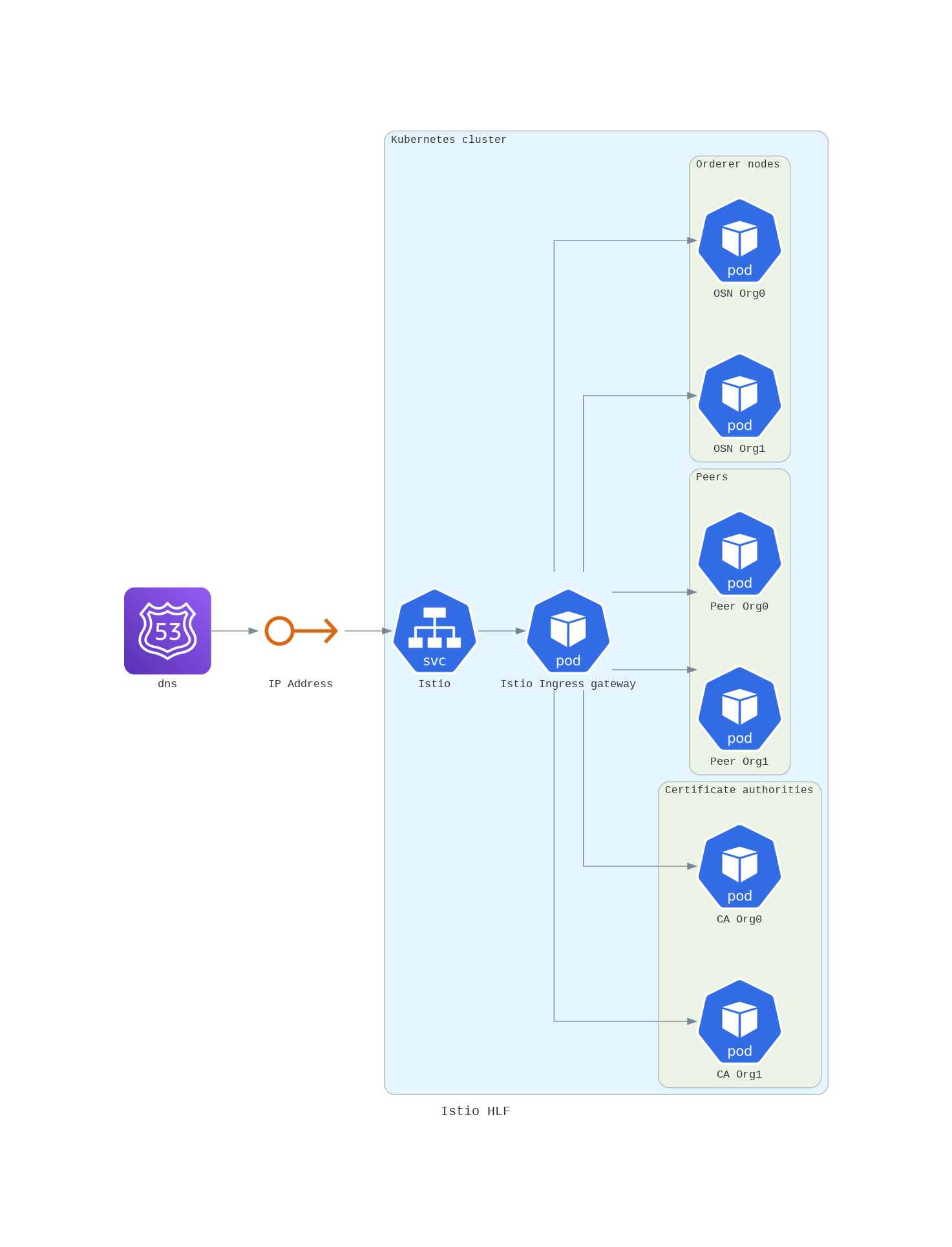
As you can see, we can note the following:
- The Istio service mesh is running in the Kubernetes cluster
- The service only has one port exposed, which is the port of the Istio ingress gateway service.
- The ingress gateway routes the traffic to the peer, OSN or CA depending on the request.
Installing istio#
You can refer to your version of choice by going to this tutorial from the istio docs to get Istio installed in your Kubernetes cluster.
Alternatively, you can just execute this command to install the latest Istio version in your Kubernetes cluster:
Locate the public IP or hostname of the ingress gateway#
Running on KinD/Minikube#
Running with load balancer IP#
Running with load balancer hostname#
Set up DNS#
Local DNS set up in Linux/Mac (for MiniKube and KinD)#
Open up /etc/hosts
Set up DNS in your DNS provider#
You will need to point the domain names you will use to the public IP of the ingress gateway, with either a A record, if you got a public IP, or a CNAME, if you got an ingress hostname
Set up the network#
Deploying a Certificate Authority#
Create the peer#
If we inspect the virtual services and gateways of Istio, we must see a record per peer.
To test that you can connect to the peer, you can use the following command to test directly from the command line(this test doesn't require DNS records to be set up):